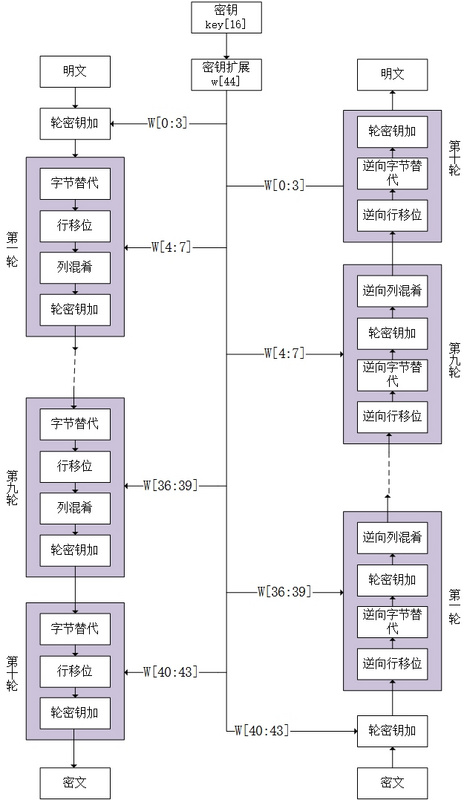
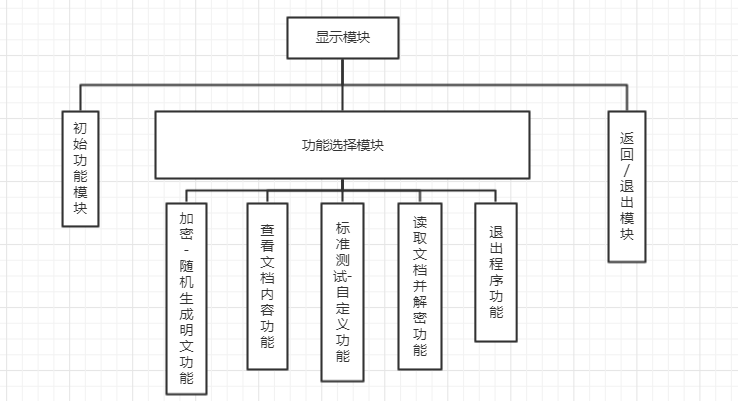
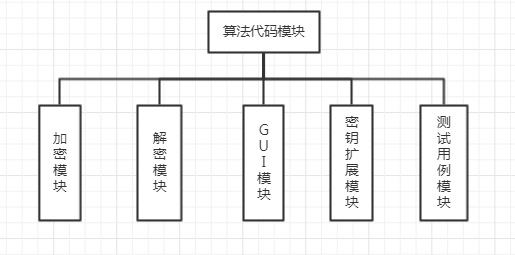
import 密钥扩展 def InvShiftRows(input1): out = [['*'for i in range(4)]for i in range(4)] for i in range(4): for j in range(4): out[i][j+i-4] = input1[i][j] return out def InvSubBytes(input1): out = [['*'for i in range(4)]for i in range(4)] map_ = [0x52, 0x09, 0x6a, 0xd5, 0x30, 0x36, 0xa5, 0x38, 0xbf, 0x40, 0xa3, 0x9e, 0x81, 0xf3, 0xd7, 0xfb, 0x7c, 0xe3, 0x39, 0x82, 0x9b, 0x2f, 0xff, 0x87, 0x34, 0x8e, 0x43, 0x44, 0xc4, 0xde, 0xe9, 0xcb, 0x54, 0x7b, 0x94, 0x32, 0xa6, 0xc2, 0x23, 0x3d, 0xee, 0x4c, 0x95, 0x0b, 0x42, 0xfa, 0xc3, 0x4e, 0x08, 0x2e, 0xa1, 0x66, 0x28, 0xd9, 0x24, 0xb2, 0x76, 0x5b, 0xa2, 0x49, 0x6d, 0x8b, 0xd1, 0x25, 0x72, 0xf8, 0xf6, 0x64, 0x86, 0x68, 0x98, 0x16, 0xd4, 0xa4, 0x5c, 0xcc, 0x5d, 0x65, 0xb6, 0x92, 0x6c, 0x70, 0x48, 0x50, 0xfd, 0xed, 0xb9, 0xda, 0x5e, 0x15, 0x46, 0x57, 0xa7, 0x8d, 0x9d, 0x84, 0x90, 0xd8, 0xab, 0x00, 0x8c, 0xbc, 0xd3, 0x0a, 0xf7, 0xe4, 0x58, 0x05, 0xb8, 0xb3, 0x45, 0x06, 0xd0, 0x2c, 0x1e, 0x8f, 0xca, 0x3f, 0x0f, 0x02, 0xc1, 0xaf, 0xbd, 0x03, 0x01, 0x13, 0x8a, 0x6b, 0x3a, 0x91, 0x11, 0x41, 0x4f, 0x67, 0xdc, 0xea, 0x97, 0xf2, 0xcf, 0xce, 0xf0, 0xb4, 0xe6, 0x73, 0x96, 0xac, 0x74, 0x22, 0xe7, 0xad, 0x35, 0x85, 0xe2, 0xf9, 0x37, 0xe8, 0x1c, 0x75, 0xdf, 0x6e, 0x47, 0xf1, 0x1a, 0x71, 0x1d, 0x29, 0xc5, 0x89, 0x6f, 0xb7, 0x62, 0x0e, 0xaa, 0x18, 0xbe, 0x1b, 0xfc, 0x56, 0x3e, 0x4b, 0xc6, 0xd2, 0x79, 0x20, 0x9a, 0xdb, 0xc0, 0xfe, 0x78, 0xcd, 0x5a, 0xf4, 0x1f, 0xdd, 0xa8, 0x33, 0x88, 0x07, 0xc7, 0x31, 0xb1, 0x12, 0x10, 0x59, 0x27, 0x80, 0xec, 0x5f, 0x60, 0x51, 0x7f, 0xa9, 0x19, 0xb5, 0x4a, 0x0d, 0x2d, 0xe5, 0x7a, 0x9f, 0x93, 0xc9, 0x9c, 0xef, 0xa0, 0xe0, 0x3b, 0x4d, 0xae, 0x2a, 0xf5, 0xb0, 0xc8, 0xeb, 0xbb, 0x3c, 0x83, 0x53, 0x99, 0x61, 0x17, 0x2b, 0x04, 0x7e, 0xba, 0x77, 0xd6, 0x26, 0xe1, 0x69, 0x14, 0x63, 0x55, 0x21, 0x0c, 0x7d] for i in range(4): for j in range(4): out[i][j] = map_[input1[i][j]] return out def InvMixColumns(inputt): col = [[0x0E,0x0B,0x0D,0x09],[0x09,0x0E,0x0B,0x0D],[0x0D,0x09,0x0E,0x0B],[0x0B,0x0D,0x09,0x0E]] out = [['*'for i in range(4)]for i in range(4)] for i in range(4): for j in range(4): out[i][j]=Mult(inputt[0][j],col[i][0])^Mult(inputt[1][j],col[i][1])^Mult(inputt[2][j],col[i][2])^Mult(inputt[3][j],col[i][3]) return out def Mult(a,b): temp = ['']*8 temp[0]=int(a) for i in range(7): if temp[i]<128: temp[i+1] = temp[i]<<1 else: temp[i+1] = ((temp[i]<<1)-0x100)^0x1B mult = 0x00 for i in range(8): mult ^= (b>>i&1)*temp[i] return mult def AddRoundKey(input_,key): temp = [['*'for i in range(4)]for i in range(4)] for i in range(4): for j in range(4): temp[i][j] = key[i][j]^input_[i][j] return temp def PrintOut(Input): temp = [] for j in range(4): for i in range(4): a = hex(Input[i][j])[2:] if len(a)<2: a = '0'+a temp.append(a) out = ''.join(map(str,temp)) return out def decode(input1): key = [[0x2b,0x28,0xab,0x09],[0x7e,0xae,0xf7,0xcf],[0x15,0xd2,0x15,0x4f],[0x16,0xa6,0x88,0x3c]] test = input1 temp = [] for j in range(4): temp.append(key[j]) for i in range(10): n = i key = 密钥扩展.KeySchedule(key,n) for j in range(4): temp.append(key[j]) out1 = AddRoundKey(test,key[-4:]) for i in range(9): out2 = InvSubBytes(InvShiftRows(out1)) k = temp[(-4)*(i+2):(-4)*(i+2)+4] out1 = InvMixColumns(AddRoundKey(out2,k)) out = InvSubBytes(InvShiftRows(out1)) out1 = AddRoundKey(out,temp[0:4]) print("明文为:"+PrintOut(out1)) def decodeWithKey(input1,Key): key = Key test = input1 temp = [] for j in range(4): temp.append(key[j]) for i in range(10): n = i key = 密钥扩展.KeySchedule(key,n) for j in range(4): temp.append(key[j]) out1 = AddRoundKey(test,key[-4:]) for i in range(9): out2 = InvSubBytes(InvShiftRows(out1)) k = temp[(-4)*(i+2):(-4)*(i+2)+4] out1 = InvMixColumns(AddRoundKey(out2,k)) out = InvSubBytes(InvShiftRows(out1)) out1 = AddRoundKey(out,temp[0:4]) print("明文为:"+PrintOut(out1)) def ReadFile(): file = open('test.txt','r') temp = [] a = file.readlines() for i in a: b = i.split( ) if b: for j in b: temp.append(j[4:]) else: return("文件为空!") input1 = [] for i in range(int(len(temp)/2)): for j in range(16): b = '0x'+temp[i*2+1][j*2:j*2+2] input1.append(int(b,16)) input2 = [['*'for n in range(4)]for n in range(4)] x = 0 for n in range(4): for m in range(4): input2[m][n] = input1[x] x = x+1 input1 = [] print("密文为:"+PrintOut(input2)) decode(input2) print('--------------------------------------------------------------------------------------') return("读取完毕!") def Trans(Input): temp = Input input1 = [] for i in range(16): b = '0x'+temp[i*2:i*2+2] input1.append(int(b,16)) input2 = [['*'for n in range(4)]for n in range(4)] x = 0 for n in range(4): for m in range(4): input2[m][n] = input1[x] x = x+1 return(input2) ''' 一维数组-->二维数组 for n in range(4): #一维数组转二维数组 input2.append(input1[n*4:n*4+4]) '''
|